Last updated on 5. December 2022
Introduction
With Microsoft Intune you can manage most of your endpoints like Windows 10/11, Android, iOS, macOS and the newest operating systems: Chrome and Linux Ubuntu. For security purposes it is a good idea to monitor changes, onboardings and compliance of devices. We will go through the configuration of redirecting the diagnostic settings into Log Analytic workspace. Once we are done with the setup, we take a look at the tables that have been created. Last but not least I will provide some KQL queries you can use for your environment.
Table of Contents
Prerequisites
Before we dive into the configuration, you have to check, if you have the following preparations:
- An Intune license
- Permission for Intune tenant (Global Administrator or Intune Service Administrator)
- An Azure subscription
- A Log Analytic workspace (we assume that Microsoft Sentinel is in use)
- Permission to Log Analytic workspace
Configuration
Open Microsoft Intune under https://endpoint.microsoft.com, navigate to Reports 🡪 Diagnostic settings and click on Add diagnostic settings.
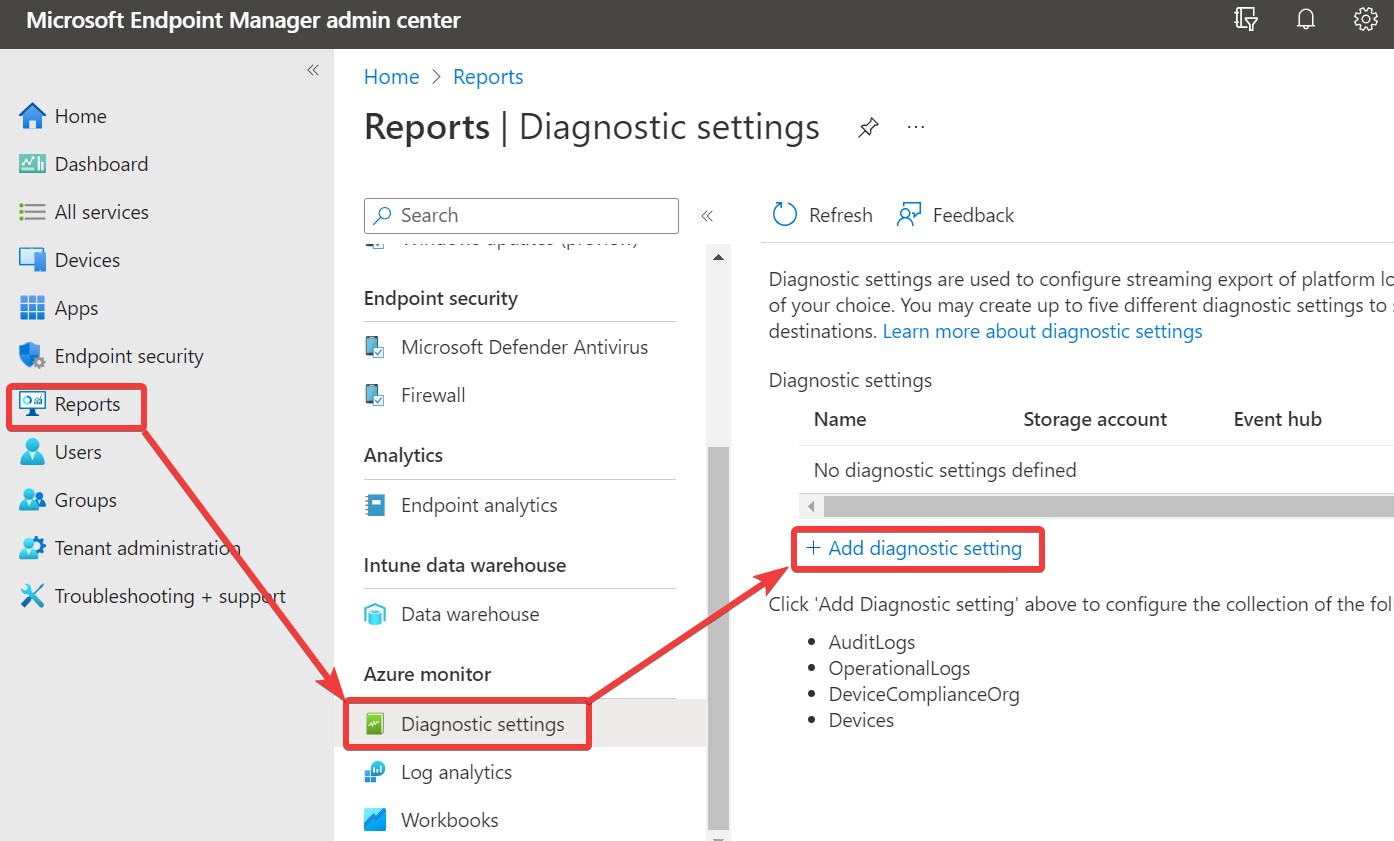
On the next page you enter the needed information. Enter a Diagnostic setting name. If you have multiple destinations, it is a good idea to define in the name, where the logs are going to. At Categories section I choose all, because the number of logs will not be so high, that I must care about costs. On Destination details choose your Log Analytic workspace in which the Microsoft Sentinel solution is installed.

After you completed the configuration, the data will flow into your chosen Log Analytic workspace. Next we will look at the tables that will be generated and which data we can find there.
KQL
The following tables get filled with data:
- IntuneAuditLogs
- Shows everything that generates a change in Intune
- IntuneDeviceComplianceOrg
- Shows details about compliant and non-compliant devices in organization
- IntuneDevices
- Shows information about status and inventory of Intune enrolled and managed devices
- IntuneOperationalLogs
- Information about failed and successful enrollments of devices and compliance state. Including user information
Getting information, which operations (create, delete, …) were performed the last 7 days:
IntuneAuditLogs
| where TimeGenerated >= ago(7d)
| extend SplitOperationName = split(OperationName, " ")
| project-away OperationName
| extend Operation = tostring(SplitOperationName[0]), OperationName = SplitOperationName[1]
| project-away SplitOperationName
| summarize count() by Operation
| render barchart
Check which operation (ClientCertificate, MobileApp, …) occurred the last 7 days:
IntuneAuditLogs
| where TimeGenerated >= ago(7d)
| extend SplitOperationName = split(OperationName, " ")
| project-away OperationName
| extend Operation = tostring(SplitOperationName[0]), OperationName = tostring(SplitOperationName[1])
| project-away SplitOperationName
| summarize count() by OperationName
| render barchart
Check the compliance state of the last 30 days:
IntuneDeviceComplianceOrg
| where TimeGenerated >= ago(30d)
| summarize count() by ComplianceState, bin(TimeGenerated, 1d)
| render timechart
If you want to filter the compliance state by operating system, you can use the following query:
let FilterOS = "Windows"; //Possible Windows, iOS, Android,
IntuneDeviceComplianceOrg
| where TimeGenerated >= ago(30d)
| where OSDescription == FilterOS
| summarize count() by ComplianceState, bin(TimeGenerated, 1d)
| render timechart
Checking Autopilot enrollment for the last 30 days:
IntuneOperationalLogs
| where TimeGenerated >= ago(30d)
| extend Autopilot = tostring(parse_json(Properties).IsAutopilot)
| where Autopilot =~ "True"
| summarize count() by Result
| render piechart
If you want to check the successful enrollments of the last 30 days including user information:
IntuneOperationalLogs
| where TimeGenerated >= ago(30d)
| where OperationName == "Enrollment" and Result == "Success"
| extend DeviceId = tostring(parse_json(Properties).IntuneDeviceId)
| join kind=leftouter IntuneDevices on DeviceId
| project DeviceName, DeviceId, UPN, OS, Result, CompliantState, Ownership, Manufacturer, Model, SerialNumber
To check out the code examples, you can find them at my GitHub: Andreas Rogge SentinelKQL
Conclusion
You can get a lot of information from the logs and it is even better to create your own workbooks to keep track of changes inside your environment. To get a better understanding of Microsoft Intune, I want to recommend you the blog of my good friend Daniel Reinartz: Cloudodidactic.com. There you’ll find everything about Endpoint Management and Microsoft Intune. Check it out or connect with him directly at LinkedIn and Twitter.
Finally, you can also connect with me on LinkedIn, Twitter and Mastodon. If you have questions or recommendations, please contact me or leave a comment 😊.
📢 By the way: I’m running out of ideas for new blog posts and need your help. Feel free to suggest your topics you’re interested in. Thx in advance 😊.


Thank you Andreas for the contribution.
What do you actually think about the security suggestions from the Microsoft Security Center, do they always make sense? In your opinion, what is a good security score that a tenant should have as a minimum? Maybe you can go into that!?
Kind regards Daniel
Hi Daniel,
like Dean replied it is the best to aim for the 100. But to be realistic this won’t be possible. The recommendations are always a good starting point and most of them should be configured, but you always have some things that do not match for your environment and should be exlcuded.
Maybe I will make an extra post about the security score :).
Best regards
Andreas
FYI, we need permissions to the subscription that contains the log analytics workspace used by Sentinel
Hi Dean, thanks for your hint. I added this to the prerequisites :).
Microsoft has thousands of people working on the security products, there recommendations are based on consensus with outside organizations, research by third parties and the metrics they obtain from thousands of customers and many million data signals. They almost always make sense and are a very good starting point. Not all of them apply to every environment, but you should have a very good reason to do something different. You should try to have a score that is always improving. It comes down to a risk evaluation and prioritization of resources. Aim for 100 and document justifications for not implementing something that is preventing you from achieving that goal. Do not think that something is not possible or that an attacker will never come after you, Make it harder for the attackers so that they give up
Hi Dean, thanks for your contribution. I absolutely agree with you.
Hello Andreas, I am trying to create a query to run in the Microsoft Sentinel to check if the Bitlocker status is disabled on the windows 10 device. Do you have maybe an example of such a query in order to create a scheduled rule in Sentinel ?
Hi,
you could try the following:
IntuneDevices| where EncryptionStatusString =~ "False"
Best regards
Andreas